Pretty much everywhere you go today, there is a WiFi network you can connect to. Whether it be at home, at the office or at the local coffee shop, there are a plethora of WiFi networks. Every WiFi network is setup with some kind of network security, either open for all to access or extremely restricted where only certain clients can connect.
When it comes to WiFi security, there are really only a couple of options you have, especially if you are setting up a home wireless network. The three big security protocols today are WEP, WPA, and WPA2. The two big algorithms that are used with these protocols are TKIP and AES with CCMP. I’ll explain some of these concepts in more detail below.
Which Security Option to Pick?
If you don’t care about all the technical details behind each one of these protocols and just want to know which one to select for your wireless router, then check out the list below. It’s ranked from most secure to least secure. The more secure option you can choose, the better.
If you’re not sure if some of your devices will be able to connect using the most secure method, I suggest you enable it and then check to see if there are any issues. I thought several devices would not support the highest encryption, but was surprised to find out they connected just fine.
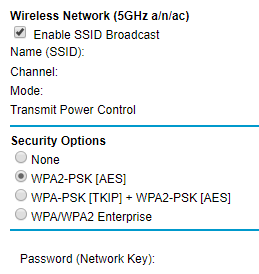
- WPA2 Enterprise (802.1x RADIUS)
- WPA2-PSK AES
- WPA-2-PSK AES + WPA-PSK TKIP
- WPA TKIP
- WEP
- Open (No security)
It’s worth noting that WPA2 Enterprise doesn’t use pre-shared keys (PSK), but instead uses the EAP protocol and requires a backend RADIUS server for authentication using a username and password. The PSK that you see with WPA2 and WPA is basically the wireless network key that you have to enter when connecting to a wireless network for the first time.
WPA2 Enterprise is way more complex to setup and is usually only done in corporate environments or in homes very technically-savvy owners. Practically, you will only be able to choose from options 2 thru 6, though most routers now don’t even have an option for WEP or WPA TKIP anymore because they are insecure.
WEP, WPA and WPA2 Overview
I’m not going to go into too much technical detail about each of these protocols because you could easily Google them for lots of more information. Basically, wireless security protocols came about starting in the late 90’s and have been evolving since then. Thankfully, only a handful of protocols were accepted and therefore it’s much easier to understand.
WEP
WEP or Wired Equivalent Privacy was released back in 1997 along with the 802.11 standard for wireless networks. It was supposed to provide confidentiality that was equivalent to that of wired networks (hence the name).
WEP started off with 64-bit encryption and eventually went all the way up to 256-bit encryption, but the most popular implementation in routers was 128-bit encryption. Unfortunately, very soon after the introduction of WEP, security researchers found several vulnerabilities that allowed them to crack a WEP key within a few minutes.
Even with upgrades and fixes, the WEP protocol remained vulnerable and easy to penetrate. In response to these problems, the WiFi Alliance introduced WPA or WiFi Protected Access, which was adopted in 2003.
WPA
WPA was actually meant to just an intermediate remedy until they could finalize WPA2, which was introduced in 2004 and is now the standard used presently. WPA used TKIP or Temporal Key Integrity Protocol as a way to ensure message integrity. This was different from WEP, which used CRC or Cyclic Redundancy Check. TKIP was much stronger than CRC.
Unfortunately, to keep things compatible, the WiFi Alliance borrowed some aspects from WEP, which ended up making WPA with TKIP insecure also. WPA included a new feature called WPS (WiFi Protected Setup), which was supposed to make it easier for users to connect devices to the wireless router. However, it ended up having vulnerabilities that allowed security researchers to crack a WPA key within a short period of time also.
WPA2
WPA2 became available as early as 2004 and was officially required by 2006. The biggest change between WPA and WPA2 was the use of the AES encryption algorithm with CCMP instead of TKIP.
In WPA, AES was optional, but in WPA2, AES is mandatory and TKIP is optional. In terms of security, AES is much more secure than TKIP. There have been some issues found in WPA2, but they are only problems in corporate environments and don’t apply to home users.
WPA uses either a 64-bit or 128-bit key, the most common being 64-bit for home routers. WPA2-PSK and WPA2-Personal are interchangeable terms.
So if you need to remember something from all this, it’s this: WPA2 is the most secure protocol and AES with CCMP is the most secure encryption. In addition, WPS should be disabled as it’s very easy to hack and capture the router PIN, which can then be used to connect to the router. If you have any questions, feel free to comment. Enjoy!
Related Posts
Founder of Help Desk Geek and managing editor. He began blogging in 2007 and quit his job in 2010 to blog full-time. He has over 15 years of industry experience in IT and holds several technical certifications. Read Aseem’s Full Bio