There’s a nice little feature built into Windows that allows you to track when someone views, edits, or deletes something inside of a specified folder. So if there’s a folder or file that you want to know who is accessing, then this is the built-in method without having to use third-party software.
This feature is actually part of a Windows security feature called Group Policy, which is used by most IT Professionals who manage computers in the corporate network via servers, however, it can also be used locally on a PC without any servers. The only downside to using Group Policy is that it is not available in lower versions of Windows. For Windows 7, you need to have Windows 7 Professional or higher. For Windows 8, you need Pro or Enterprise.
The term Group Policy basically refers to a set of registry settings that can be controlled via a graphical user interface. You enable or disable various settings and these edits are then updated in the Windows registry.
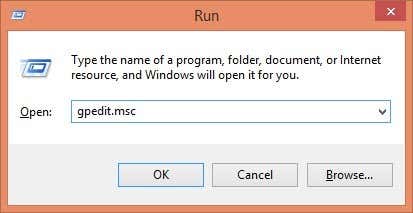
In Windows XP, to get to the policy editor, click on Start and then Run. In the text box, type “gpedit.msc” without the quotes as shown below:
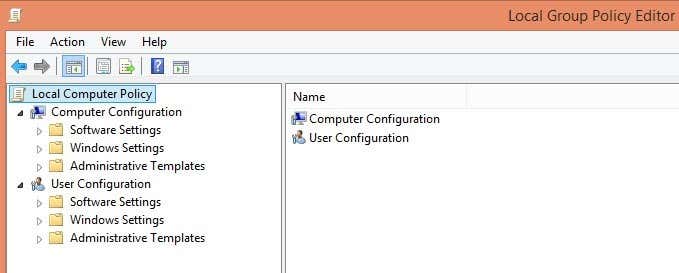
In Windows 7, you would just click on the Start button and type gpedit.msc into the search box at the bottom of the Start Menu. In Windows 8, simply go to the Start Screen and start typing or move your mouse cursor to the far top or bottom right of the screen to open the Charms bar and click on Search. Then just type in gpedit. Now you should see something that is similar to the image below:
There are two main categories of policies: User and Computer. As you might have guessed, the user policies control the settings for each user whereas the computer settings will be system wide settings and will effect all users. In our case we’re going to want our setting to be for all users, so we’ll expand the Computer Configuration section.
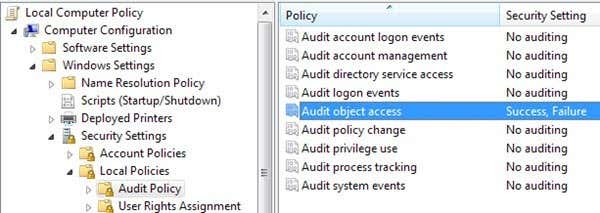
Continue expanding to Windows Settings -> Security Settings -> Local Policies -> Audit Policy. I’m not going to explain much of the other settings here since this is primarily focused on auditing a folder. Now you’ll see a set of policies and their current settings on the right hand side. Audit policy is what controls whether or not the operating system is configured and ready to track changes.
Now check the setting for Audit Object Access by double clicking on it and selecting both Success and Failure. Click OK and now we’re done the first part which is telling Windows that we want it to be ready to monitor changes. Now the next step is to tell it what EXACTLY we want to track. You can close out of the Group Policy console now.
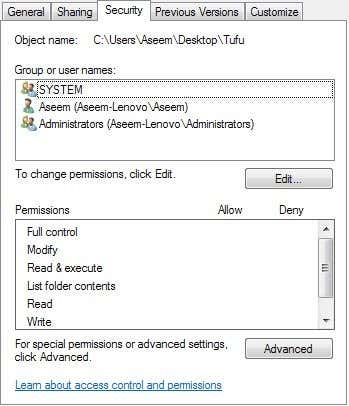
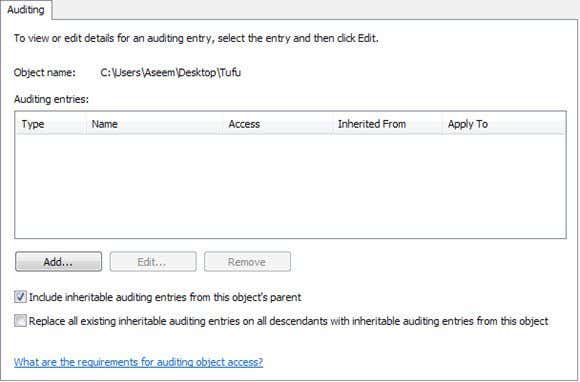
Now navigate to the folder using Windows Explorer that you would like to monitor. In Explorer, right click on the folder and click Properties. Click on the Security Tab and you see something similar to this:
Now click on the Advanced button and click on the Auditing tab. This is where we’ll actually configure what we want to monitor for this folder.
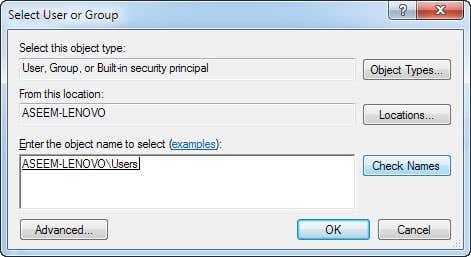
Go ahead and click the Add button. A dialog will appear asking you to select a User or Group. In the box, type in the word “users” and click Check Names. The box will automatically update with the name of the local users group for your computer in the form COMPUTERNAME\Users.
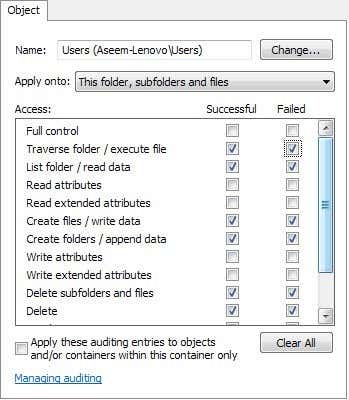
Click OK and now you’ll get another dialog called “Audit Entry for X“. This is the real meat of what we’ve been wanting to do. Here is where you’ll select what you want to watch for this folder. You can individually choose which types of activity you want to track, such as deleting or creating new files/folders, etc. To make things easier, I suggest selecting Full Control, which will automatically select all the other options below it. Do this for Success and Failure. This way, whatever is done to that folder or the files within it, you will have a record.
Now click OK and click OK again and OK one more time to get out of the multiple dialog box set. And now you have successfully configured auditing on a folder! So you might ask, how do you view the events?
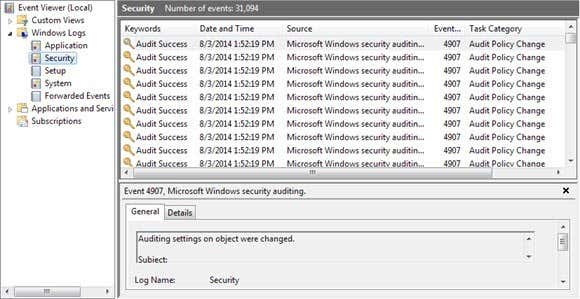
In order to view the events, you need to go to the Control Panel and click on Administrative Tools. Then open up the Event Viewer. Click on the Security section and you’ll see a large listing of events on the right hand side:
If you go ahead and create a file or simply open the folder and click the Refresh button in the Event Viewer (the button with the two green arrows), you’ll see a bunch of events in the category of File System. These pertain to any delete, create, read, write operations on the folders/files you are auditing. In Windows 7, everything now shows up under File System task category, so in order to see what happened, you’ll have to click on each one and scroll through it.
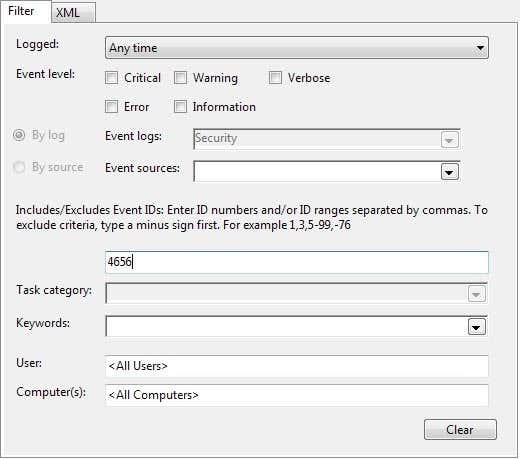
In order to make it easier to look through so many events, you can put a filter and just see the important stuff. Click on the View menu at the top and click on Filter. If there is no option for Filter, then right-click on the Security log in the left-hand page and choose Filter Current Log. In the Event ID box, type in the number 4656. This is the event associated with a particular user performing a File System action and will give you the relevant information without having to look through thousands of entries.
If you want to get more information about an event, simply double click on it to view.
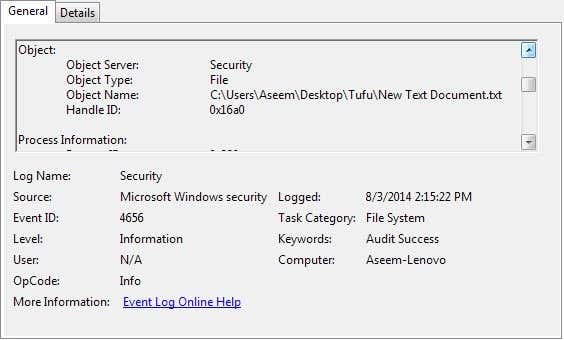
This is the information from the screen above:
A handle to an object was requested.
Subject:
Security ID: Aseem-Lenovo\Aseem
Account Name: Aseem
Account Domain: Aseem-Lenovo
Logon ID: 0x175a1
Object:
Object Server: Security
Object Type: File
Object Name: C:\Users\Aseem\Desktop\Tufu\New Text Document.txt
Handle ID: 0x16a0
Process Information:
Process ID: 0x820
Process Name: C:\Windows\explorer.exe
Access Request Information:
Transaction ID: {00000000-0000-0000-0000-000000000000}
Accesses: DELETE
SYNCHRONIZE
ReadAttributes
In the example above, the file worked on was New Text Document.txt in the Tufu folder on my desktop and the accesses that I requested were DELETE followed by SYNCHRONIZE. What I did here was delete the file. Here’s another example:
Object Type: File
Object Name: C:\Users\Aseem\Desktop\Tufu\Address Labels.docx
Handle ID: 0x178
Process Information:
Process ID: 0x1008
Process Name: C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
Access Request Information:
Transaction ID: {00000000-0000-0000-0000-000000000000}
Accesses: READ_CONTROL
SYNCHRONIZE
ReadData (or ListDirectory)
WriteData (or AddFile)
AppendData (or AddSubdirectory or CreatePipeInstance)
ReadEA
WriteEA
ReadAttributes
WriteAttributes
Access Reasons: READ_CONTROL: Granted by Ownership
SYNCHRONIZE: Granted by D:(A;ID;FA;;;S-1-5-21-597862309-2018615179-2090787082-1000)
As you read through this, you can see I accessed Address Labels.docx using the WINWORD.EXE program and my accesses included READ_CONTROL and my access reasons were also READ_CONTROL. Usually, you’ll see a bunch more accesses, but just focus on the first one as that’s usually the main type of access. In this case, I simply opened the file using Word. It does take a little testing and reading through the events to understand what’s going on, but once you have it down, it’s a very reliable system. I suggest creating a test folder with files and performing various actions to see what shows up in the Event Viewer.
That’s pretty much it! A quick and free way to track access or changes to a folder!
Related Posts
- How to Boot into Safe Mode in All Versions of Windows
- How to Reset Your Computer Password If You Lock Yourself Out
- Transfer Files from Windows XP, Vista, 7 or 8 to Windows 10 using Windows Easy Transfer
- How to Change the Clock To Military Time in Windows
- Best Ways to Quickly Hide Windows Applications
Founder of Help Desk Geek and managing editor. He began blogging in 2007 and quit his job in 2010 to blog full-time. He has over 15 years of industry experience in IT and holds several technical certifications. Read Aseem’s Full Bio