Knowing that someone is monitoring your computer is pretty scary, but it’s perhaps even scarier not knowing how to tell if it’s even happening. But it does happen, and could very well happen to you too if you’re not actively blocking it.
If someone is monitoring your computer, they might have been doing so for some time and could have seen much of what you were doing. They may have stolen passwords you typed, bank details you opened in your browser, photos stored on the phone you plugged in…the list goes on.

If you think your computer has been hijacked and everything you’re doing is being watched and/or tracked, keep reading to learn how to verify that your computer is being monitored, and what to do to stop it.
Important: If you already know that someone is actively monitoring your computer right now, disconnecting from the internet will terminate their connection instantly. If you can do that, go for it and then read through this page to see what you can do without the internet to stop them remotely accessing you the next time you connect to the internet.
Is My Computer Being Monitored?
Below are several methods for seeing if your computer is being monitored.
Use An Anti-Spyware Program
One of the best methods is also a preventative measure – install an anti-spyware program. They detect spyware but also usually everything from open network ports to webcam monitoring, and they not only detect these things but also actively block them.
Tip: You can block webcam access yourself too, from your web browser.
Here are some good options:
- SpywareBlaster
- Avast Free Antivirus
- Malwarebytes
- SUPERAntiSpyware
- Spybot
You’ll be alerted each time the program finds a breach, and you can usually either enable a block to prevent it from happening again or you’ll be told that the program has already blocked it for you.
For example, if a keylogger has been sending your keystrokes to a hacker in another country, the anti-spyware tool will likely block it and then tell you so.
Tip: It’s recommended to install the free trial of the program you pick from the list above. All of them are free for the most part, but if you want more features (one of which might be able to catch your computer being monitored remotely), you might need to get the full version. Installing the trial gives you a taste of the additional features.
View Active Connections To The Internet
The next best way to see if someone is monitoring your computer is to view all of the active connections your computer is making with something on the internet.
TCPView is a great way to do this in Windows. It’s pretty straightforward in that you see which process on your computer is connected to a specific remote address. Since there might be a lot of entries here, it’s best to shut down your web browser and cease as much internet activity as you can. Then sort the list by Remote Port to find anything out of place.
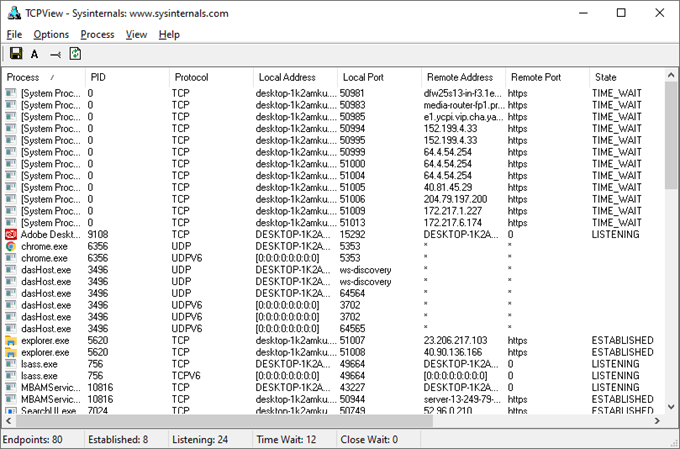
If TCPView shows that your computer is being monitored remotely, right-click the process to end the connection, and then do some research to learn how it got on your computer so you will know how to delete it for good.
The Wireshark packet analyzer is another option that also runs on Macs, but the learning curve is rather high.
Check For Open Ports
Your computer connects to the internet via network ports. Common ones include ports 80, 21 and 443. But depending on what you’ve installed to your computer and whether you have port forwarding rules set up, there could be a lot more ports open.
The issue with having lots of ports open (or specific ones that you aren’t using) is that someone could take advantage of them to communicate with your computer remotely to send/receive viruses and other files, passwords, images, etc.
Use a port checker like this one to scan the ports on your network. You can close ports by logging into your router or blocking them with a firewall program.
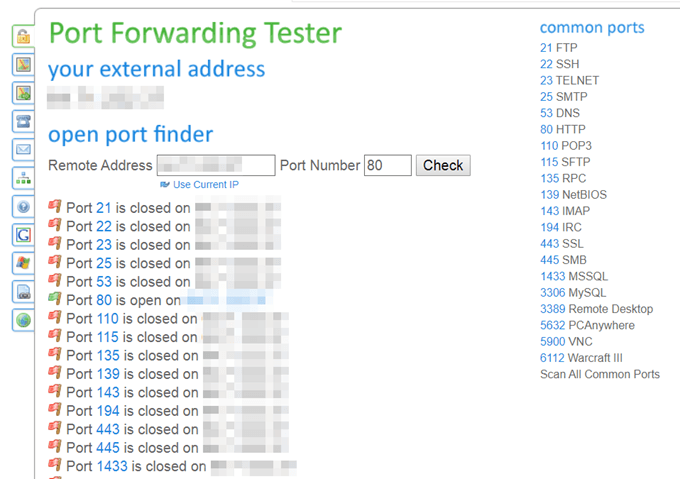
Tip: A router can track and monitor internet activity. If you’re an admin on your network and you want to do that, be sure to check out that article.
Review Installed Programs
A common way a computer starts being monitored remotely is through malware. Maybe you installed a program that you fully intended on using or that you do actively use, or maybe the program was installed as bundleware and you don’t even know it’s there.
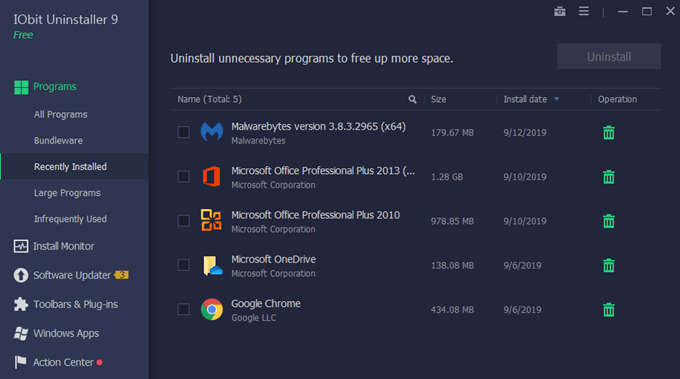
Regardless, you should do a check of the programs that are currently installed. If there are apps you don’t recognize or programs that you don’t even use anymore, promptly remove them. One of the best ways to do that is with IObit Uninstaller.
Check The Wi-Fi Security
Not all Wi-Fi networks require a password, especially public hotspots. If you’re using a laptop or a desktop with Wi-Fi, check the network you’re connected to to see if it’s secure.
While this doesn’t exactly explain right away that your computer is being monitored, it does make it more likely if a password isn’t necessary to use it. An open, unencrypted Wi-Fi network means that someone else on that network has a much better chance at seeing that you’re connected to it and monitoring your wireless traffic to pick up things like the passwords your type into websites, the images you upload online, etc.
See How to View Saved WiFi Passwords on Windows for directions on locating the area of Windows that shows the Wi-Fi security.
Monitoring Your Computer Might Be Required
Isn’t that a scary thought! It’s important to realize that depending on your situation, there might be rules in place that demand that your activities be watched. If so, there’s likely little you can do to stop it.
For example, if you use a computer at work, there’s probably an employee monitoring policy that has to be upheld for security purposes. This might mean that they’re watching not only what you do on the web but also what gets plugged into your computer, which programs you open, how often you’re using each application, how often your computer goes to sleep, etc.
If this is happening to you, there’s likely not much you can do because you probably can’t install anti-tracking software or remove programs from the machine.
It’s common for companies to include their own spyware blockers, virus detectors, and other tools to protect all of the company’s computers and other resources. So you probably don’t need to worry about installing something on your individual computer (unless you work in the IT department) if you’re worried about external monitoring while you’re at work.
Related Posts
Founder of Help Desk Geek and managing editor. He began blogging in 2007 and quit his job in 2010 to blog full-time. He has over 15 years of industry experience in IT and holds several technical certifications. Read Aseem’s Full Bio
