I purchased a new Cisco SG300 10-port Gigabit Ethernet managed switch a few months back and it’s been one of the best investments for my small home network. Cisco switches have so many features and options that you can configure to granularly control your network. In terms of security, their products stand out.
With that said, it’s very interesting how unsecure a Cisco switch is fresh out of the box. When you plug it in, it either grabs an IP address from a DHCP server or assigns itself an IP address (usually 192.168.1.254) and uses cisco for the username and password. Yikes!
Since most networks use the 192.168.1.x network ID, your switch is completely accessible to anyone on the network. In this article, I’m going to talk about five immediate steps you should take after you plug in your switch. This will ensure your device is secure and configured properly.
Note: This article is geared towards home or small office users who are new to Cisco switches. If you’re Cisco engineer, you’re going to find all of this very simplistic.
Step 1 – Change Default Username & Password
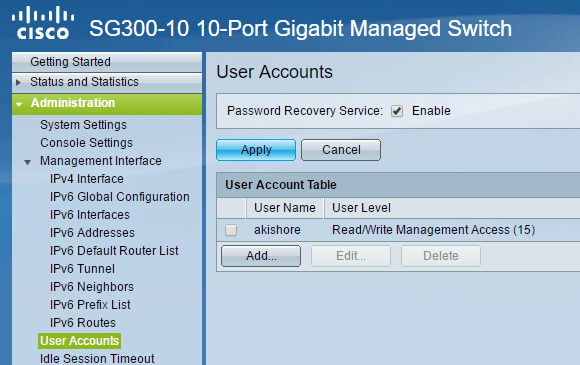
This is obviously the first step and the most important. Once you log into the switch, expand Administration and then click on User Accounts.
The first thing you’ll want to do is add another user account so that you can then delete the original cisco user account. Make sure that you give the new account full access, which is Read/Write Management Access (15) in Cisco parlance. Use a strong password and then log out of the cisco account and login using your new account. You should now be able to remove the default account.
It’s also probably a good idea to enable the Password Recovery Service, just in case you forget the password you set. You’ll need console access to the device to reset the password.
Step 2 – Assign a Static IP Address
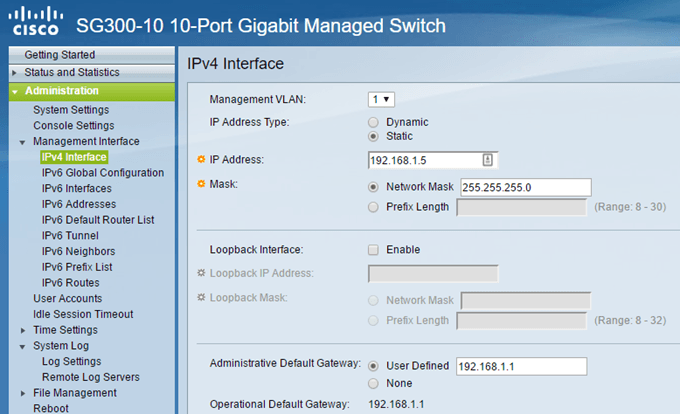
By default, the switch should have a static IP address already, but if not, you should manually set it. It’ll also be necessary if you’re not using the 192.168.1 network ID. To do this, expand Administration – Management Interface – IPv4 Interface.
Choose Static for IP Address Type and enter in a static IP address. This will make it much easier to manage your switch also. If you know the default gateway for your network, go ahead and add that in also under Administrative Default Gateway.
It’s also worth noting that the IP address is assigned to a virtual LAN interface, meaning you can access the device using the IP address regardless of which port is connected on the switch as long as those ports are assigned to the Management VLAN selected at the top. By default, this is VLAN 1 and all ports are by default in VLAN 1.
Step 3 – Update the Firmware
Since my cheap Netgear router can check the Internet for a software update and automatically download and install it, you would think a fancy Cisco switch could do the same. But you’d be wrong! It’s probably for security reasons why they don’t do this, but it’s still annoying.
To update a Cisco switch with new firmware, you have to download it from the Cisco website and then upload it to the switch. In addition, you then have to change the active image to the new firmware version. I really do like this feature as it provides a bit of protection in case something goes wrong.
To find the new firmware, just Google your switch model with the word firmware at the end. For example, in my case, I just Googled Cisco SG300-10 firmware.
I’ll be writing up another article on how to upgrade the firmware for a Cisco router as there are a couple of things you want to be aware of before doing so.
Step 4 – Configure Secure Access
The next step I recommend is enabling only secure access to your switch. If you are a command line pro, you really should disable the web GUI altogether and turn on SSH access only. However, if you need the GUI interface, you should at least set it to use HTTPS rather than HTTP.
Check out my previous post on how to enable SSH access for your switch and then login using a tool like puTTY. For even more security, you can turn on public key authentication with SSH and login using a private key. You can also restrict access to the management interface by IP address, which I will write about in a future post.
Step 5 – Copy Running Config to Startup Config
The last thing you want to get used to when using any Cisco device is copying the running config to the startup config. Basically, all the changes you make are only stored in RAM, which means when you reboot the device, all the settings will be lost.
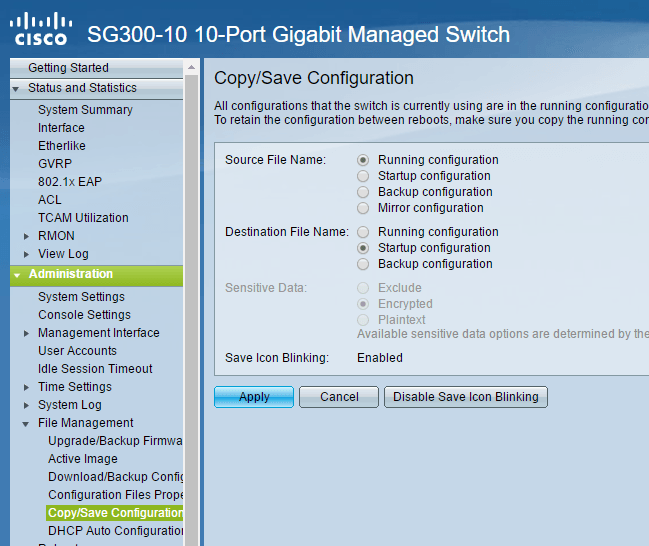
In order to permanently save the configuration, you have to copy the running config to startup config, the latter of which is stored in NVRAM or non-volatile RAM. To do this, expand Administration, then File Management and then click on Copy/Save Configuration.
The default settings should be correct, so all you have to do is click on Apply. Again, make sure you do this anytime you make any kind of change to your switch.
Those were some really basic configuration steps for getting your switch initially setup and secured. I’ll be posting more advanced tutorials soon on other aspects of the switch. If you have any questions, feel free to comment. Enjoy!