There are many reasons to track Windows user activity, including monitoring your children’s activity across the internet, protection against unauthorized access, improving security issues, and mitigating insider threats.
Here will discuss tracking options for a variety of Windows environments, including your home PC, server network user tracking, and workgroups.
Check Your Web History
If you want to know which sites someone on your computer (such as your children) are visiting, you can find that information via the browser history. Even though tech-savvy users might know ways to hide this history, it doesn’t hurt to check.
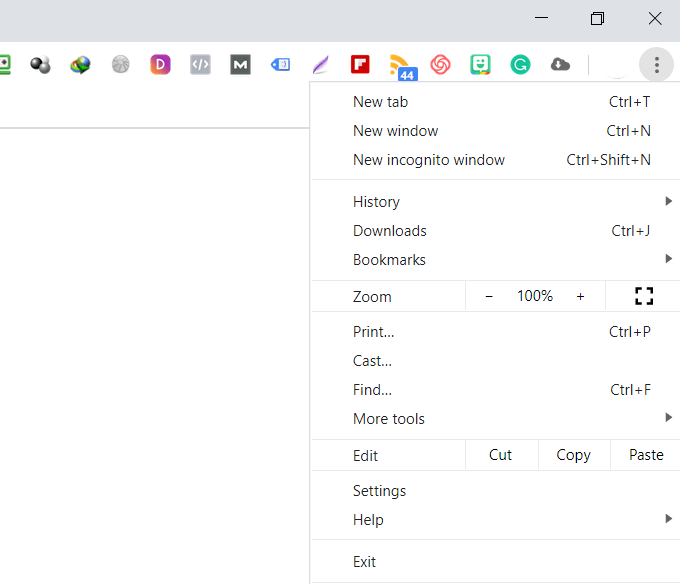
- Using Google Chrome, click on the three dots in the upper right-hand corner and click History.
- Another way to access your computer history in Chrome is to use the Ctrl + H shortcut.
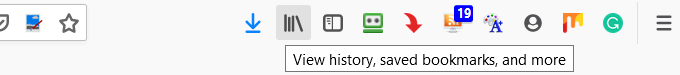
- In Firefox, navigate to the icon in the top bar that looks like the image below and click on it.
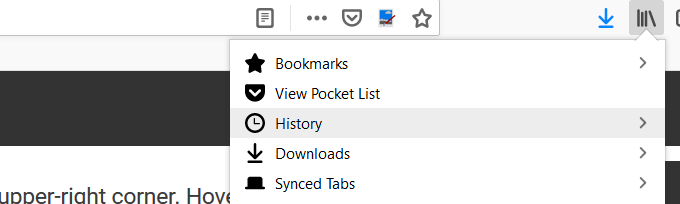
- Then click History.
- In Microsoft Edge, in the top-right corner of the window, look for and click on the shooting star icon. Then click on History.
Windows Events
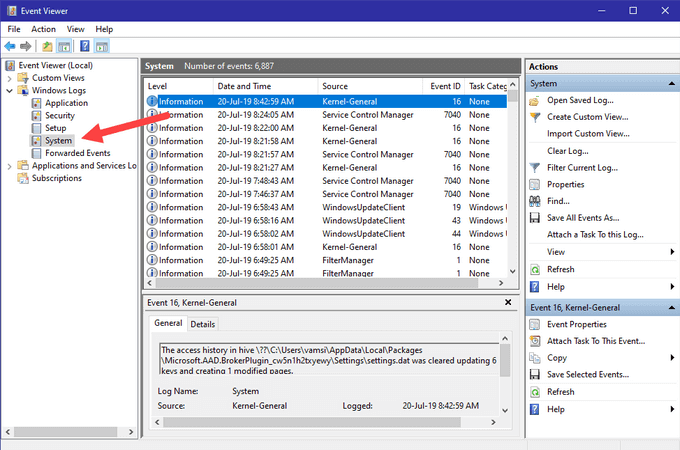
Windows keeps track of all user activity on your computer. The first step to determine if someone else is using your computer is to identify the times when it was in use.
- From the Start Menu, type event viewer and open it by clicking on it.
- To expand the Windows Logs folder, click on Event Viewer (local).
- Expand Windows Logs by clicking on it, and then right-click on System.
- Double-click on Filter Current Log and open the dropdown menu for Event Sources.
- Scroll down to Power-Troubleshooter and tick the box next to it. Then click OK.
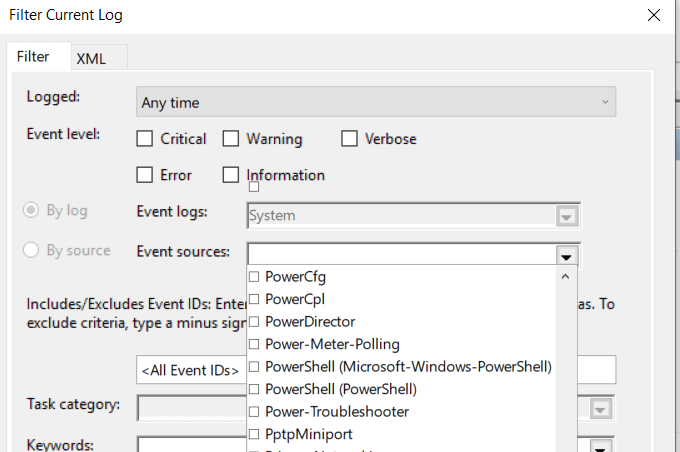
- The Windows Event Viewer will show you when your computer was brought out of sleep mode or turned on. If you weren’t using it during these times, someone else was.
How To Identify Suspicious Activity On a Windows Server
If you are running an environment with several Windows servers, security is vital. Auditing and tracking Windows activities to identify suspicious activity is paramount for numerous reasons, including:
- The prevalence of malware and viruses in Windows OS
- Some applications and programs require users to disable some antivirus and local firewalls
- Users often don’t disconnect remote desktop sessions, leaving the system vulnerable to unauthorized access
It’s better to take preventative measures than to wait until an incident occurs. You should have a robust security monitoring process in place to see who is logging onto your server and when. This will identify suspicious events in the Windows server security reports.
What To Look Out For In Your Windows Reports
As the administrator of a server, there are several events to keep an eye on to protect your network from nefarious Windows user activity, including:
- Failed or successful attempts of remote desktop sessions.
- Repeated login attempts resulting in password lockouts.
- Group or audit policy changes you didn’t make.
- Successful or failed attempts to log into your Windows network, member services, or domain controller.
- Deleted or stopped existing services or new services added.
- Registry settings changed.
- Event logs cleared.
- Disabled or changed Windows firewall or rules.
As discussed above, events are recorded in the event log in Windows. The three main types of native logs are:
- Security.
- Application.
- System.
XpoLog7
XpoLog7 is an automated log management tool to provide:
- Log data analysis
- Automatic detection of problems
- Proactive monitoring of rules and events
The basic plan is free forever for 0.5GB/day. For those needing more features, Xpolog7 also offers several tiered pricing options.

How To Track User Activity In Workgroups
Workgroups are organized networks of computers. They enable users to share storage, files, and printers.
It is a convenient way to work together and easy to use and administer. However, without proper administration, you are opening your network to potential security risks that can affect all participants of the workgroup.
Below are tips on how to track user activity to increase your network security.
Use Windows Audit Policy
Follow the steps below to track what workgroup participants are doing on your network.
- Open Run by holding down the Windows key and R.
- Type secpol.msc in the box next to Open: and click OK.
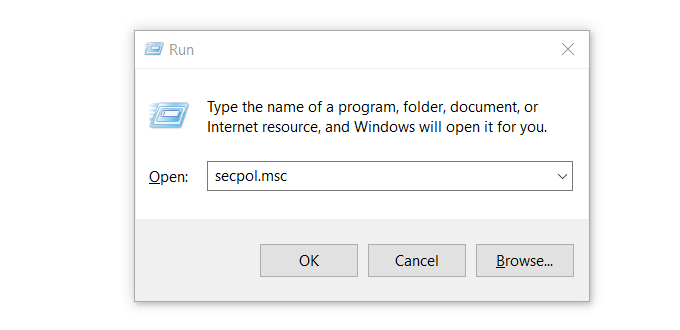
This will open the Local Security Policy window.
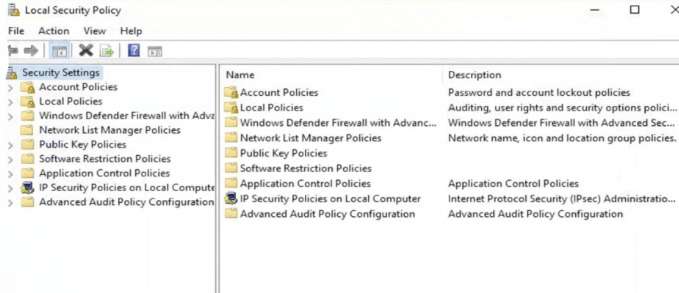
- From the column on the left, double-click Security Settings. Then expand the Local Policies setting by clicking on it.
- Open Audit Policy, and then on the menu in the right pane you will see many Audit entries that are set to Not Defined.
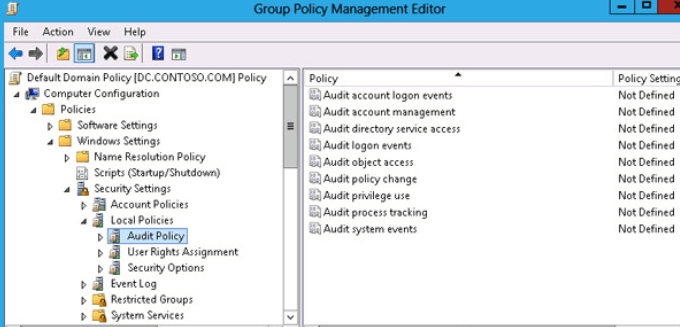
- Open the first entry. From the Local Security Settings tab, check Success and Failure under Audit these attempts. Then click Apply and OK.
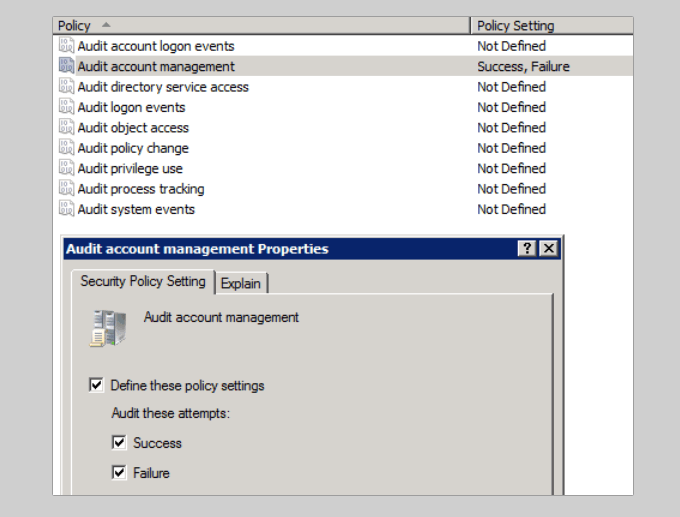
Repeat the steps above for all entries to track user activity in workgroups. Keep in mind that all the computers in your workgroup must be properly protected. If one computer gets infected, all others connected to the same network are at risk.
Keyloggers
Keylogger programs monitor keyboard activity and keep a log of everything typed. They are an effective way to monitor Windows user activity to see if someone has been intruding on your privacy.
Most people who use keylogger programs do so for malicious reasons. Because of this, your anti-malware program will likely quarantine it. So you will need to remove the quarantine to use it.
There are several free keylogger software programs for you to choose from if you are in the market.
Related Posts
- Preparing for Windows 10 End of Support: Upgrading to Windows 11
- How to Fix a “This file does not have an app associated with it” Error on Windows
- How to Fix an Update Error 0x800705b4 on Windows
- How to Resolve “A JavaScript error occured in the main process” Error on Windows
- How to Fix the Network Discovery Is Turned Off Error on Windows