
Fixed: Discord Is Stuck on a Gray Screen (11 Methods)
Does your Discord app get stuck on the gray screen and won’t go past it? Your app has run into…
Read our step-by-step guides and practical tips for mastering tech with ease. We cover everything from device setup and troubleshooting to software hacks and productivity tricks. Empower yourself with solutions for everyday tech challenges.

Does your Discord app get stuck on the gray screen and won’t go past it? Your app has run into…

A “Download error - 0x80248007” message on your Windows 11 PC suggests that your Windows or driver update has failed…
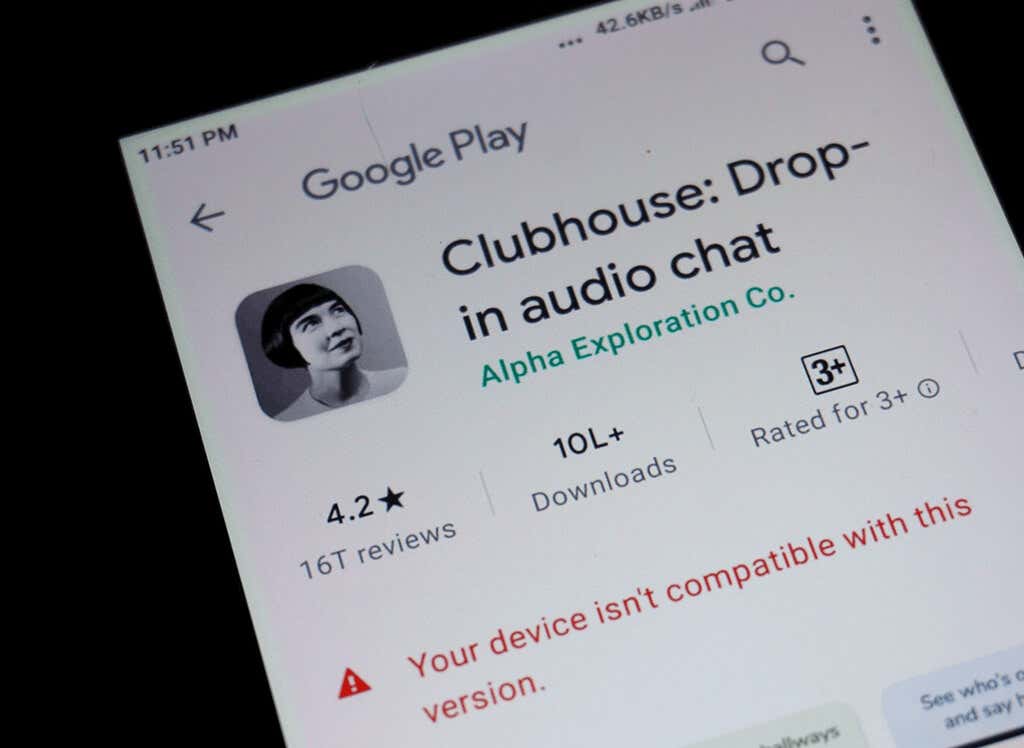
While downloading specific apps on your Android device, you might find that the Play Store displays a “Your device isn't…
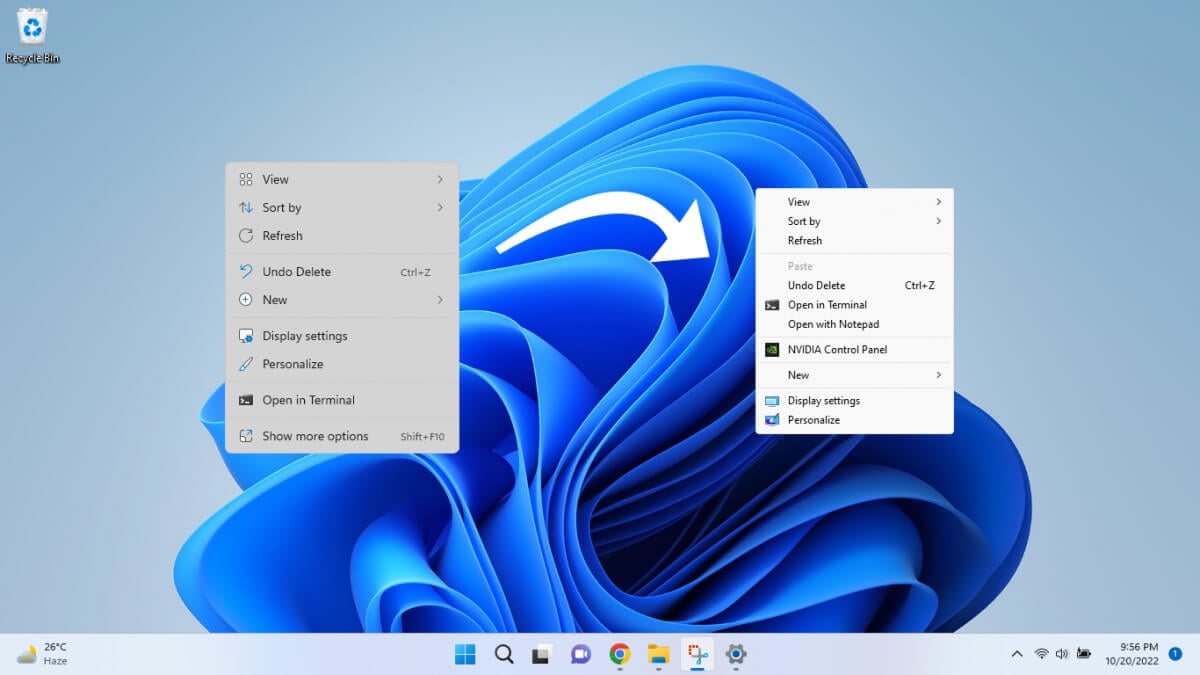
While many like the streamlined right-click context menu of Windows 11, some are less than pleased with the truncated menu.…

Does your Chromebook get stuck on a white screen (with or without the Chrome logo) during startup? This post will…

Your Chromebook might shut down without warning if it’s overheating, has a faulty battery, or runs an outdated operating system.…

VirtualBox lets you run multiple operating systems on your computer in virtual machines. The virtualization software supports Windows, Linux, macOS,…

Do you need to use an application only available for Windows on your Chromebook? We’ll show you how to use…

Do you see a "Download English US Update - Waiting for network connection" error related to Speech Services by Google…

Google Assistant is helpful, but if you're uncomfortable with an always-listening AI, you can turn it off on all your…

Most people don’t bother with latitude and longitude to identify a location. However, it’s still a sure-fire way to note…

Even if you use the Google app daily, you might be missing one of its most brilliant features. Google Assistant…

Is Linux crashing your low-end or budget Chromebook? Does running Linux apps slow your Chromebook’s performance or cause other glitches?…

Running a virtual machine on Linux allows you to use other operating systems and software without dual boot or partitioning…

Linux, the open-source operating system darling, has long captivated the hearts of developers, programmers, and tech enthusiasts alike. Its versatility…
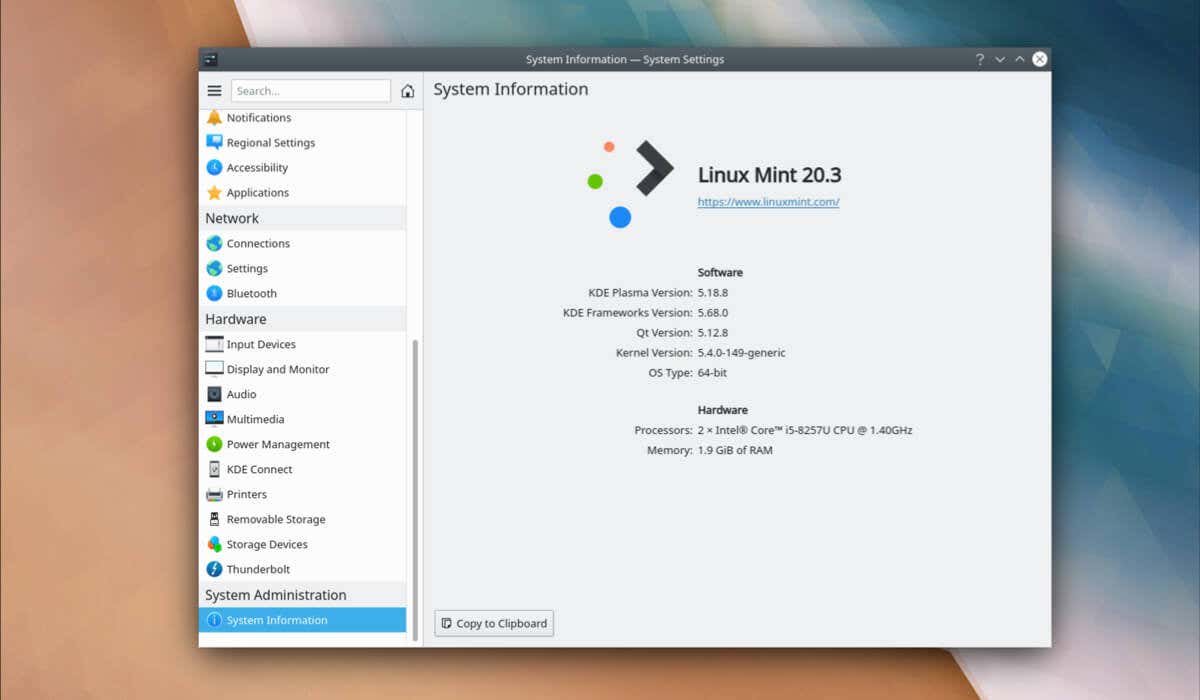
Linux Mint is a popular, user-friendly Linux distribution that provides a variety of features to make your computing experience more…
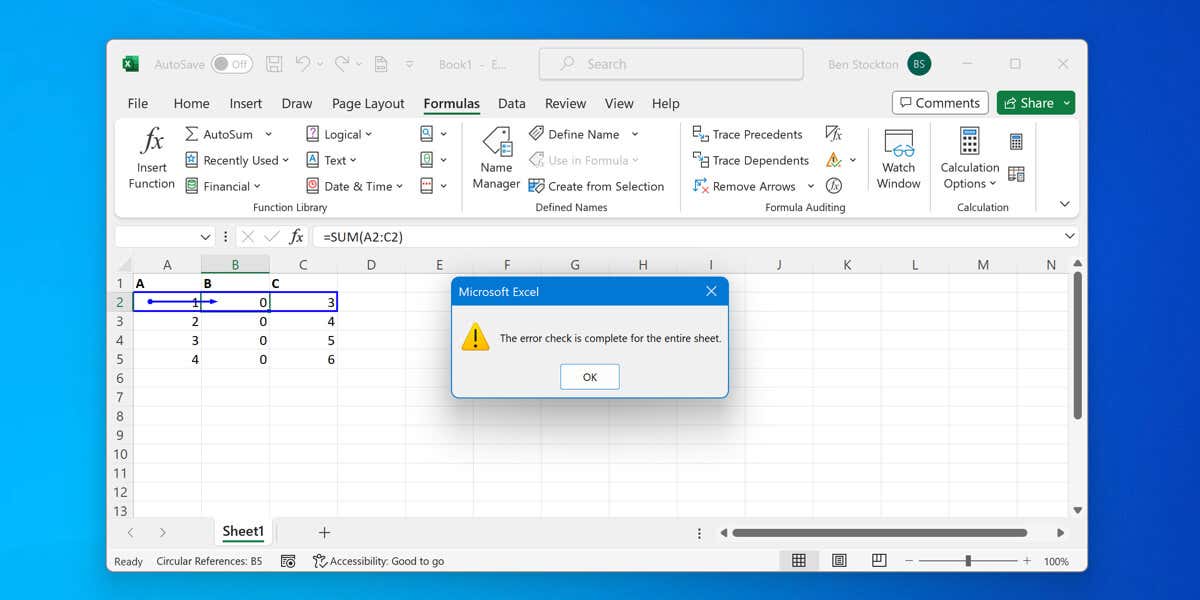
There’s no point going around in circles with your data. In Excel, any attempt to create a loop with your…

Headers and footers in Word documents are great places to store extra document information that also allows for easy navigation.…

Phishing emails are scams that try to get you to hand over personal information by pretending to be from a…

Not many Excel users name their cells, constant values, or formulas inside the worksheet. However, there’s a purpose to Excel…

The clock is ticking for Windows 10 users! On October 14, 2025, Microsoft will end support for Windows 10, meaning…
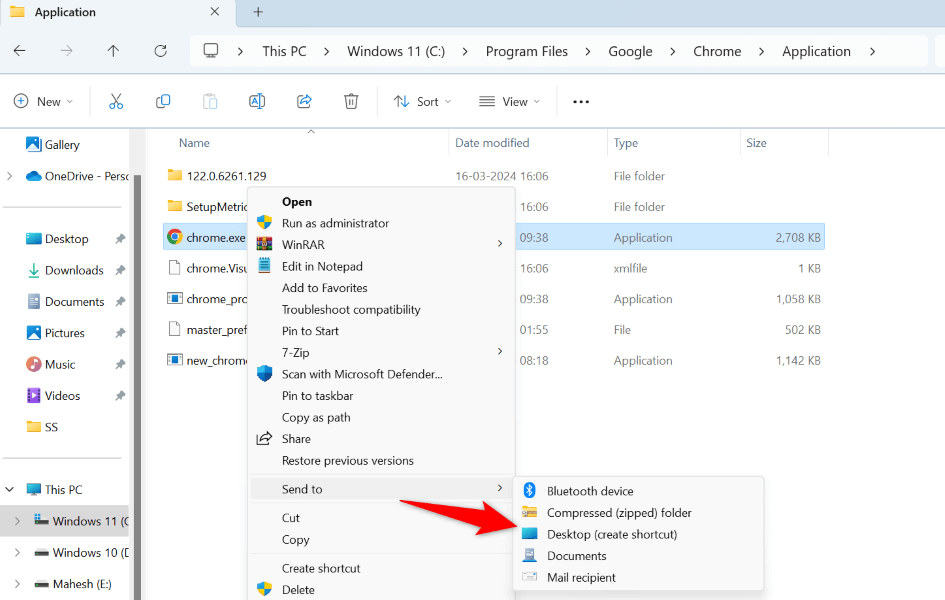
Are you trying to launch an app, game, or file but keep getting a “This file does not have an…
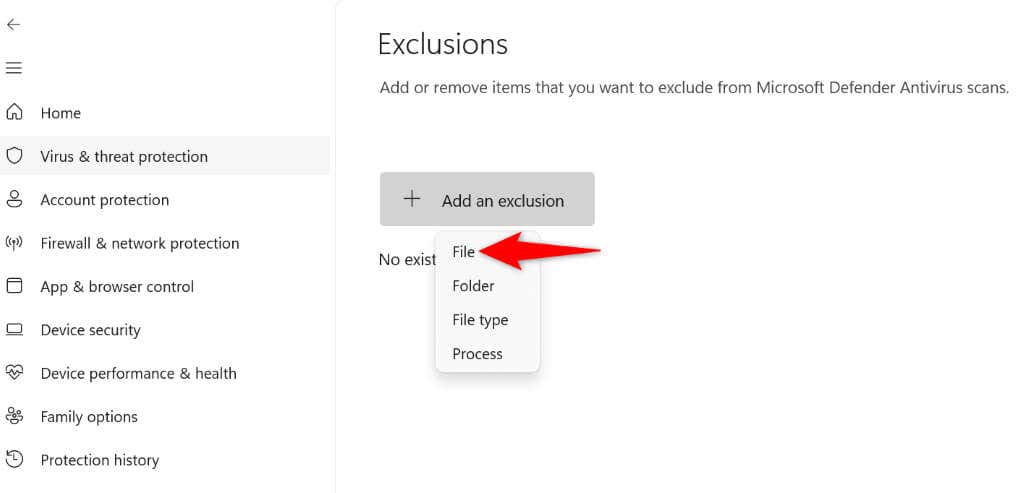
Both Windows 11 and Windows 10 display an update error 0x800705b4 when a system update fails to install. If this…
If you’ve run into an “A JavaScript error occurred in the main process” notification while installing or launching an app,…

Imagine trying to log into your Windows 11 PC only to find your desktop is gone, your files are missing,…

The clock is ticking for Windows 10 users! On October 14, 2025, Microsoft will end support for Windows 10, meaning…

Are you trying to launch an app, game, or file but keep getting a “This file does not have an…

Microsoft OneDrive is an excellent choice for backing up and syncing your files to the cloud on Windows. It integrates…

Whether your messages aren’t synching or you have trouble locating new files, refreshing Microsoft Teams helps fix these and other…

Changing your PC's display settings might not always give you the results you're looking for. You might end up with…

Keeping your video drivers up-to-date is crucial for optimizing performance in Windows 11. But there are also rare instances where…
Encountering a 0x80073701 error usually indicates your PC’s Windows Update components aren’t working correctly. There are other reasons this error…

There seem to be all sorts of takes on the traditional keyboard design these days, from melty ergonomic models to…

Getting a new computer is an exciting experience, like purchasing a new car---you can't wait to test its capabilities. At…
RAM (Random Access Memory) is a key component of any computer, but there’s more to it than capacity or speed.…

If Windows refuses to shut down, it may be due to the Task Host Window, a system service that manages…

Are you tired of seeing the same old folder and shortcut icons on your Windows 11 or 10 PC? You…
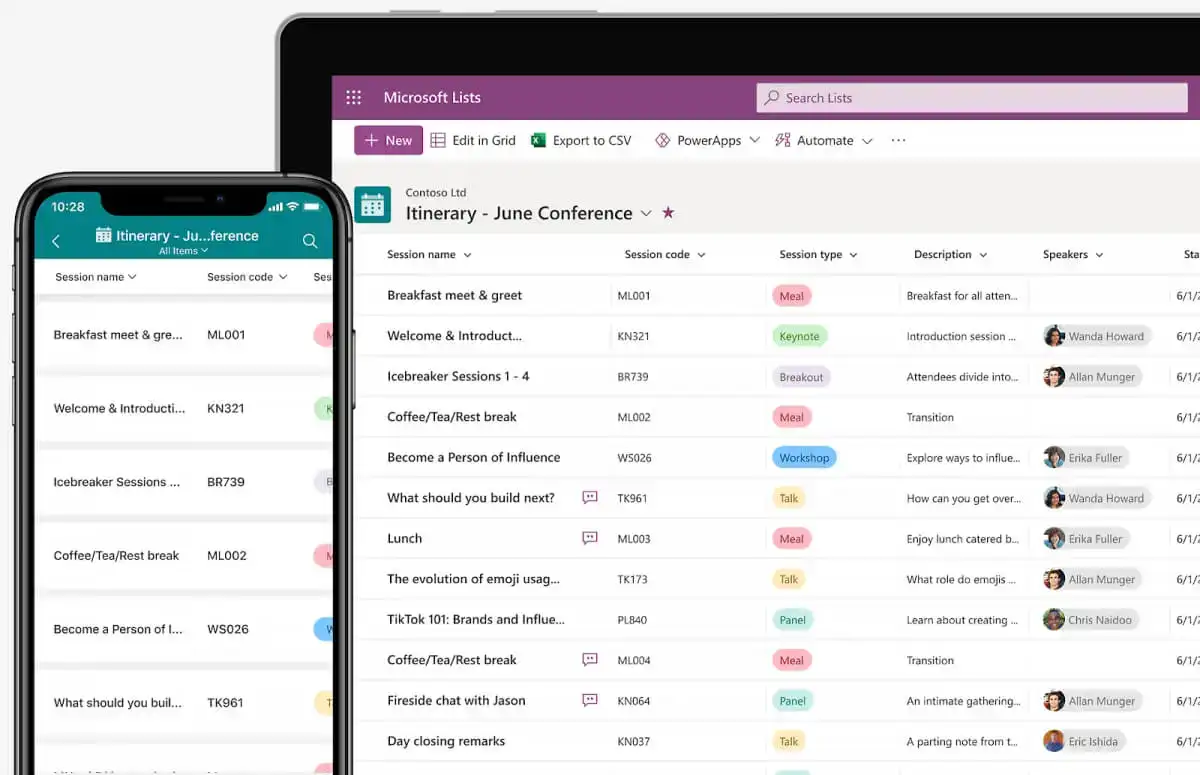
While Microsoft already had a Kanban board-style application (Microsoft Planner), the newly released Microsoft Lists fulfills the need for a…
Redlining documents is the process of making changes to a document that allows other users, such as editors or reviewers,…
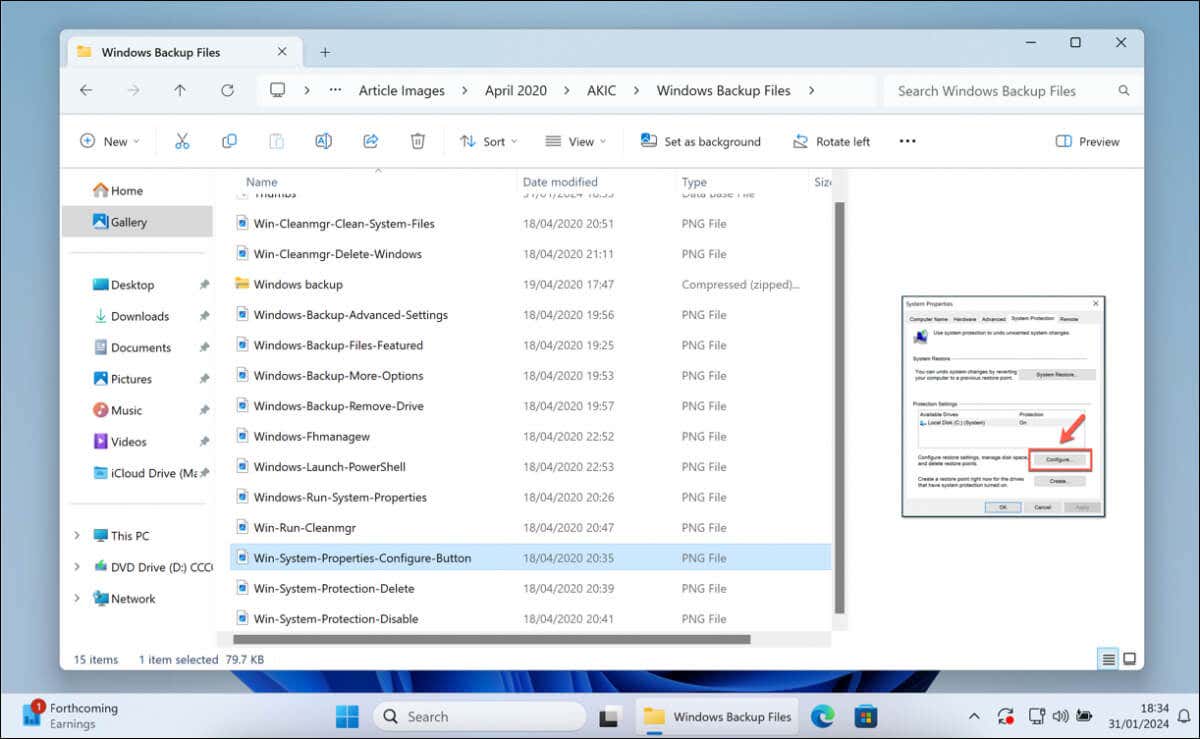
Your Windows operating system understands that not every file type is the same. For instance, how you want to view…