Viruses have gotten more sophisticated, and so have the security features designed to combat them. The Kernel-mode Hardware-enforced Stack Protection is another such advanced defense present in Windows 11.
The name may be a mouthful, but it accurately describes the function of the security feature in technical terms. But what does that translate to in plain English? Is it even necessary? Let’s find out.
A Crash Course Into Stack Buffer Overflow
Before you can understand what hardware-enforced stack protection does, you must understand what stack buffer overflow attacks are, because that’s what it is trying to guard against. And before you can grasp that, you need to have an idea of what the Stack even means.
In simplest terms, the stack refers to the memory addresses being used by an active program. Every running process or application is assigned a stack, including system processes. Data is written and read from this stack, maintaining a separation from other processes using the memory.
But sometimes things go wrong, and a program spills over its demarcated stack. This is called a Stack Overflow error and can lead to all sorts of weird behavior as the process tries to read data not meant for it.
What Are Stack Buffer Overflow Attacks?
So far we have discussed stack overflow in the context of an unintended error. But this phenomenon can also be deliberately exploited to control programs and processes by feeding them unexpected inputs.
Such memory attacks – also known as Return-Oriented Programming or ROP attacks – are rather difficult for the program to detect since the very memory it reads its instructions from is compromised. Especially if the program in question is a core system process that cannot rely on any other low-level program to verify itself.
This makes stack buffer overflow attacks a very dangerous category of cyber threats. One being taken advantage of by a wave of new viruses.
The Solution: Kernel Mode Hardware Enforced Stack Protection
We have talked about how the lack of a low-level baseline for system processes to compare themselves leaves them as vulnerable to stack buffer overflow attacks as a normal application. But what if we could establish a baseline in the underlying hardware itself?
That’s exactly what Kernel mode Hardware-enforced stack protection does. Using virtualization, the CPU is isolated from the running applications and processes on your computer, safeguarding it against any tampering through memory manipulation.
This is because the stack addresses are also held in a parallel Shadow stack that is not exposed to the rest of the PC. Every time a kernel-mode process (basically low-level system functions) reads information, the address is confirmed with the copy stored in the shadow stack as well. The process is terminated if there is any discrepancy.
What Are the Requirements for Running Hardware Enforced Stack Protection On Your PC?
As a low-level feature with specific hardware dependencies, this enhanced stack protection has steep hardware requirements. Only processors that support the latest CPU virtualization features can implement this security measure.
For Intel, this means the Control-Flow Enforcement Technology (CET), while AMD simply calls it AMD shadow stacks. Even when your processor does support the feature, CPU Virtualization and Memory Integrity must be enabled for it to take effect.
Keep in mind, however, that virtualization-related security features might also have a minor impact on the performance of the computer. This is primarily why these features don’t usually come enabled by default.
What to do if Kernel-Mode Hardware-Enforced Stack Protection is Off?
There are many reasons why kernel-mode hardware-enforced stack protection might be disabled on your PC. Your processor might not support the feature, or it may just require manual activation.
But before you jump to find the option and try enabling it, take a moment to consider if you even need to. Because for most users, core isolation and related security features might be unnecessary.
Normal viruses and malware are dealt with effectively by the Microsoft Windows Defender. Unless your system houses sensitive data that might be specifically targeted by dedicated hackers, you don’t really need stack protection on your PC.
But if you do want to enable the feature, here is how to do it:
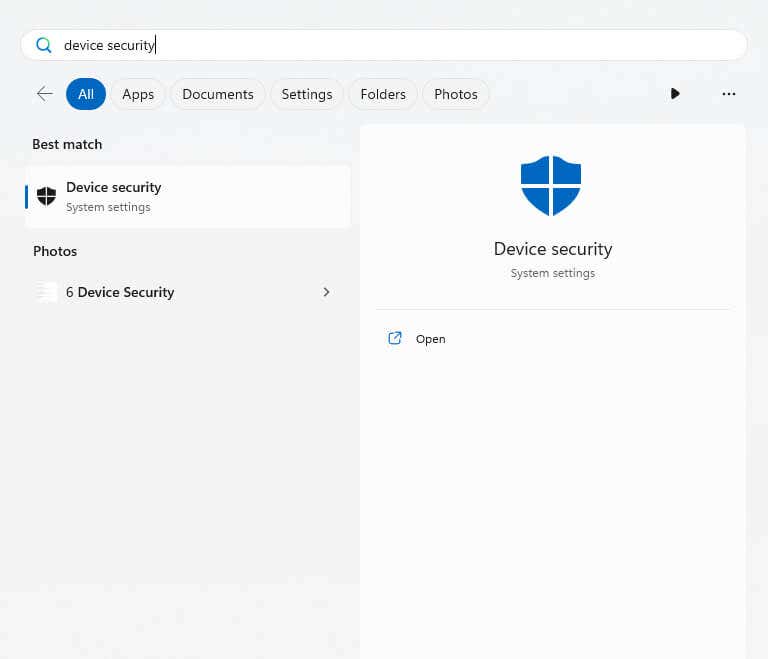
- First, you need to open the Device Security window. You can do this by navigating to Settings > Privacy & security > Windows security and then clicking on the Device security option, or just search for it in the Start menu.
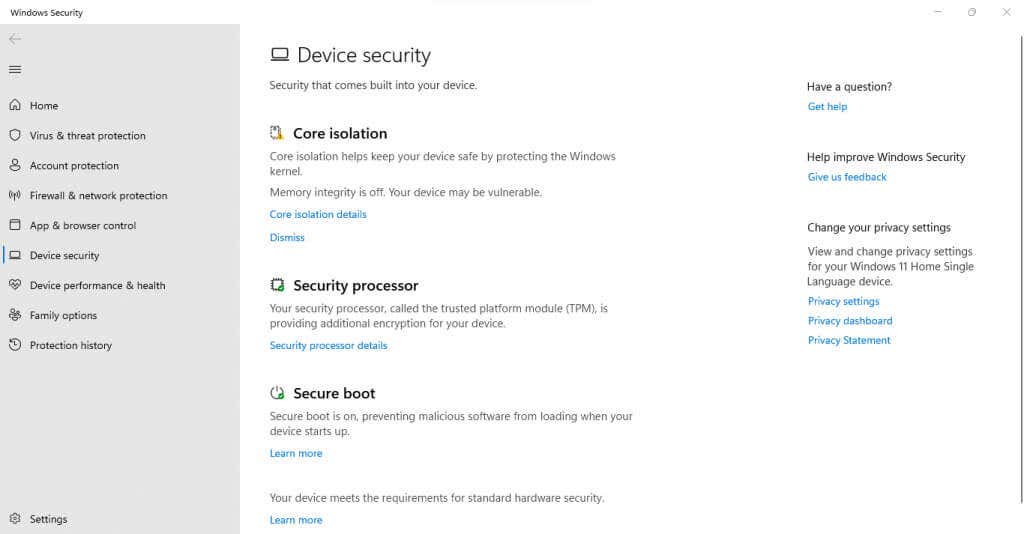
- Device security lists all hardware-related security features on your device like Core isolation, Trusted Platform Module (TPM), and Secure Boot. The hardware-enforced stack protection feature is a subset of Core isolation. To view it, click on the Core isolation details option.
- Now what you see on this window diverges according to your system’s hardware configuration. On PCs that don’t support hardware-enforced stack protection at all, you will see no option (like in our test system).
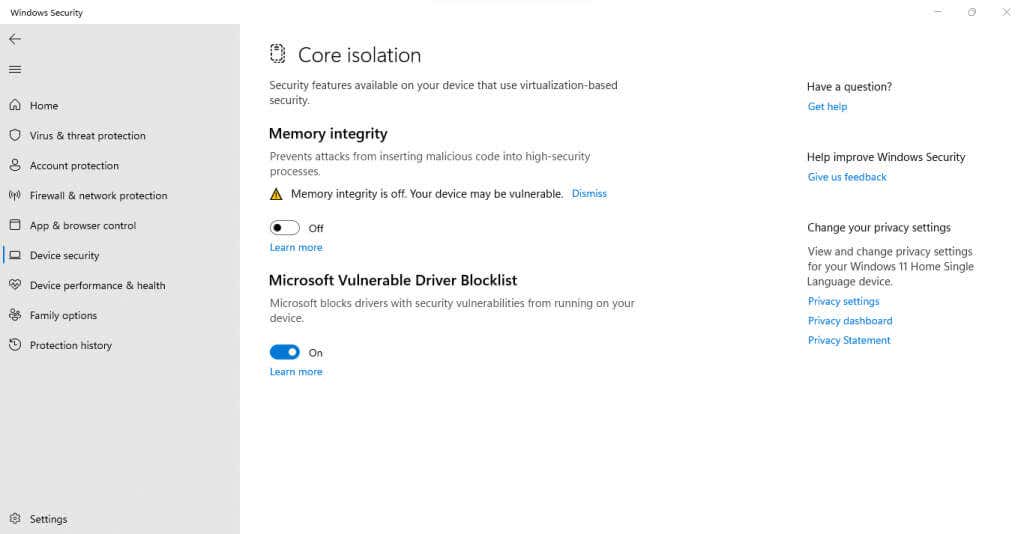
If you see the option but it is grayed out, you just need to enable virtualization in the BIOS and enable Memory integrity as well. Once you do that, you can switch on Kernel-mode Hardware-enforced Stack Protection. Restart your PC and the change will take effect.
Occasionally the feature will be blocked by incompatible drivers, at which point you can remove your update the drivers. Although this issue has become less common after the past few updates.
Is Kernel Mode Hardware Enforced Stack Protection Worth it in Windows 11?
Windows 11 comes with a slew of advanced security features designed to deter even the most dedicated hacking attempts. Most of these features like TPM or Secure Boot come enabled by default on supported systems.
But the Kernel-mode Hardware-enforced Stack Protection is different. Since it can have a slight impact on performance and is not essential for most systems, it has to be manually enabled. Not to mention the more stringent hardware requirements for the feature, unlike TPM which is near universal even on somewhat older chips.
So if you see the option in your Device security window and are concerned about low-level virus attacks, you can enable hardware-enforced stack protection to ensure perfect security. If the performance impact becomes noticeable, you can always disable it again.
Related Posts
Levin Roy is a software engineer who loves writing about technology. Whether it is Windows tips-and-tricks or in-depth guides about application development, Levin uses his practical experience and technical skills to create articles that can help solve tricky problems. Read Levin’s Full Bio